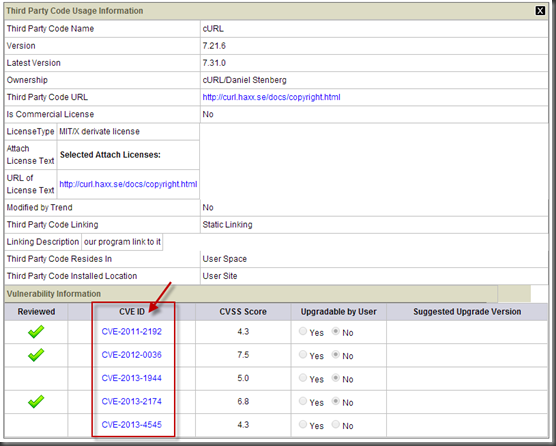
#9: Using Components with Known Vulnerabilities
If there is number in Vulnerability column, that means there are vulnerability on that specfic 3rd Party Component.
Click View to see following info, CVE ID:
CVE: Common Vulnerabilities and Exposures
Search CVE database on Google,
Example, CVE-2014-1266, known vulnerability for Apple
But hacker will use Exploit Database
http://www.exploit-db.com/exploits/25719/
Blind SQL Injection
http://www.exploit-db.com/exploits/21546/
#8: Cross-Site Request Forgery (CSRF)
One-Click Attack, Session Riding
1. User has success authenticated
2. Hacker send a link to that user
3. User click on that link, but not authenticated by himself, to access the website
Exercise, send a link to your friend, following for example, to see if your friend can open that directly.
What can be achieved?
1. Adding movies to his rental queue
2. Adding a movie to the top of his rental queue
3. Changing the name and address on the account
4. Enabling/disabling extra movie information
5. Changing the e-mail address and password on the account
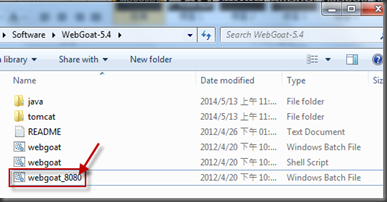
Launch WebGoat in local machine, by double click webgoat_8080
Open Chrome, type in URL: http://127.0.0.1:8080/WebGoat/attack
Name & Password: guest
Click Start WebGoat button to launch it
http://127.0.0.1:8080/WebGoat/attack?Screen=52&menu=900&transferFunds=5000
Homework: How do I prevent it?
1. Add a hidden CSRFToken in every page.
2. Generate a CAPTCHA to client, enforce user to type manually.
Example 2: steps like below
1. Observation HTTP Post on Victim site
2. PHP post parameters on Phishing site
3. Generate the URL and send to Users
4. Wait for the User to click
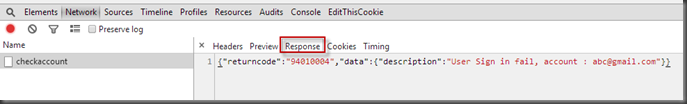
Step 1: Observation HTTP Post on Victim site
https://www.directpass.com/signin
Request URL
Request Payload
Response Message
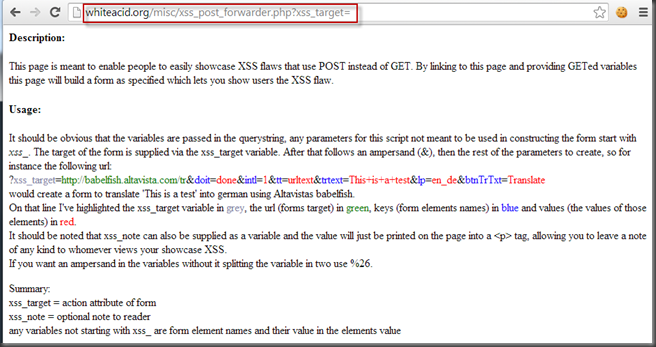
Step 2: PHP post parameters on Phishing site
http://whiteacid.org/misc/xss_post_forwarder.php?xss_target=
Step 3: Generate the URL and send to Users
Step 4: Wait for the User to click
#7: Missing Function Level Access Control
Example, mobile to view picture do not need authentication
Exercise, login WebGoat, try if can view the Admin Functions
Hint: add parameter in URL to do GET request
#6: Sensitive Data Exposure
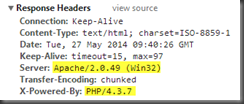
Identify the web technology of the following sites?
http://Hackyourselffirst.troyhunt.com
Homework: How to prevent it?
1. Using SSL, https
2.
#5: Security Mis-configuration
There are 4 major areas
Setting
Admin Page
User Account
Demo Application
How to prevent it? When Deployment
1. Environment Hardening (patch)
2. Vulnerability Management
3. Operational Enablement
Google: index of /admin
Homework: how if I want to search by Google, but don’t want to show too much?
1. Use Nofollow meta tag to tell search engine not to spider
2. Use Noindex meta tag to tell search engine not to index this page
3. Use X-Roobot
Reference:





















沒有留言:
張貼留言